Accessing Azure Active Directory Graph API
In this blog post I’m building an application that requires Azure Graph access.
Setup
I’m starting off with a new .NET Core console application to keep the example simple.
dotnet new console -o testGraphClientI’m adding two NuGet packages to the project file, to help with authenticating against Active Directory.
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<OutputType>Exe</OutputType>
<TargetFramework>netcoreapp2.1</TargetFramework>
</PropertyGroup>
<ItemGroup>
<PackageReference Include="Microsoft.Graph" Version="1.12.0" />
<PackageReference Include="Microsoft.IdentityModel.Clients.ActiveDirectory" Version="4.4.2" />
</ItemGroup>
</Project>Azure Active Directory
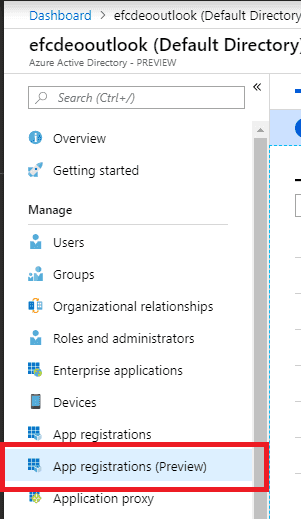
Now before I get into the code, I’m going to skip ahead to registering your application. I’m using the Application Registrations Preview on Azure.
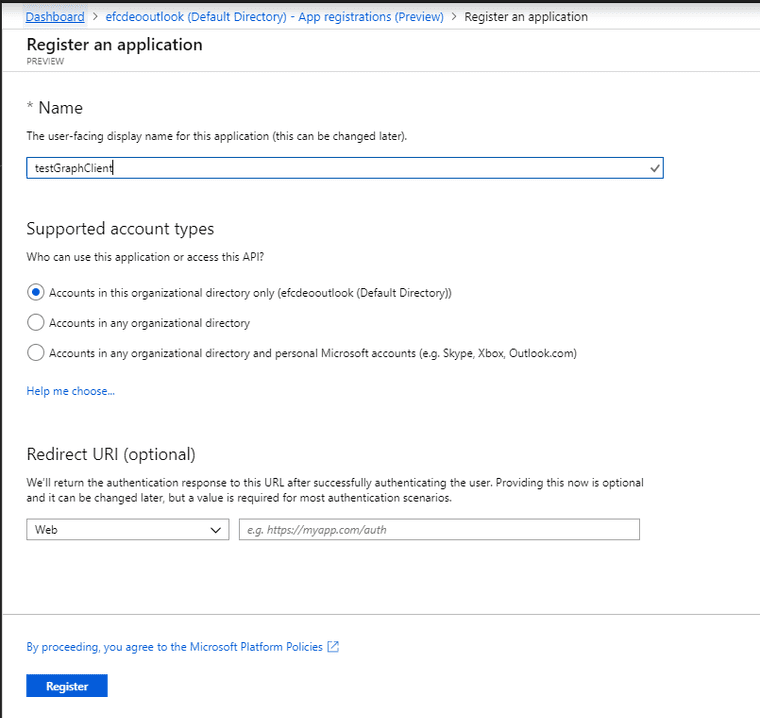
Let’s go ahead and register the new application. I’m leaving the Redirect empty.
Make a note of the ApplicationID.
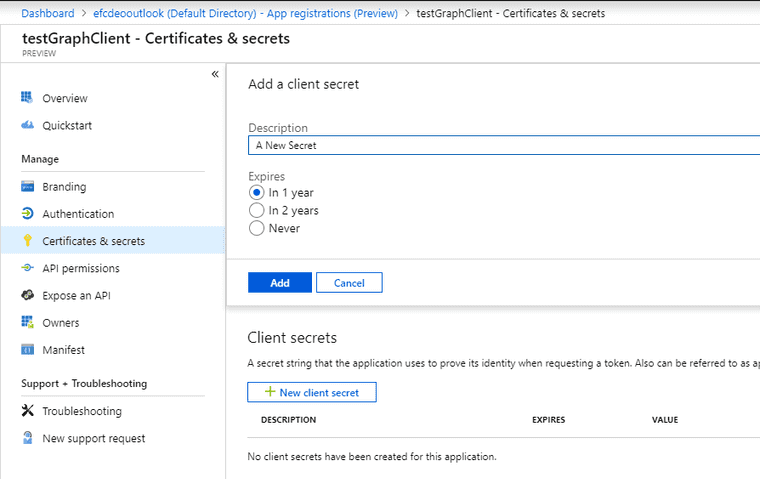
Create a new Client Secret and take a note of it, because once created you’ll never be able to see it again.
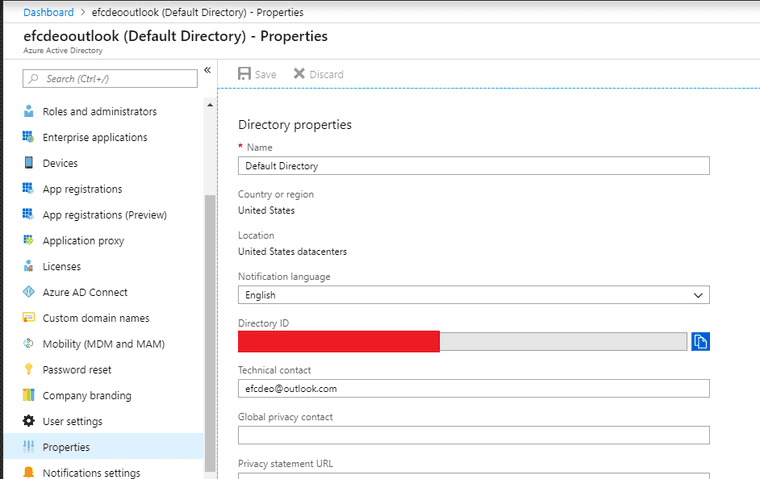
Take a note of the Azure Tenant ID which can be found under the properties as the Directory ID.
Granting Application Permissions
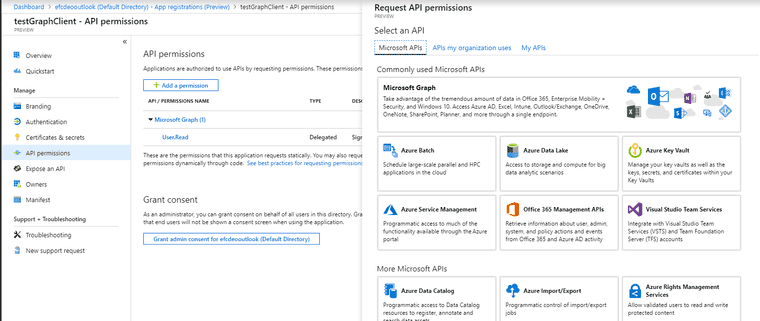
Make sure that you are logged in as an Admin. Under the created application registration from above, there is an option to Add API Permissions.
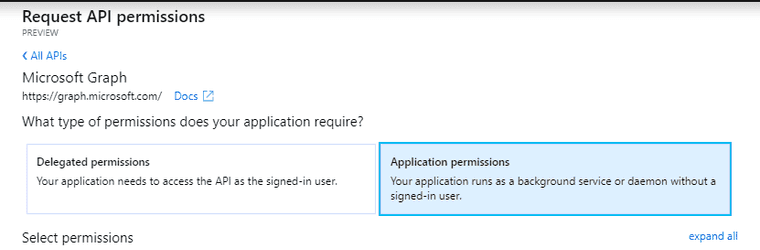
Select Azure Graph, and then Application Permissions.
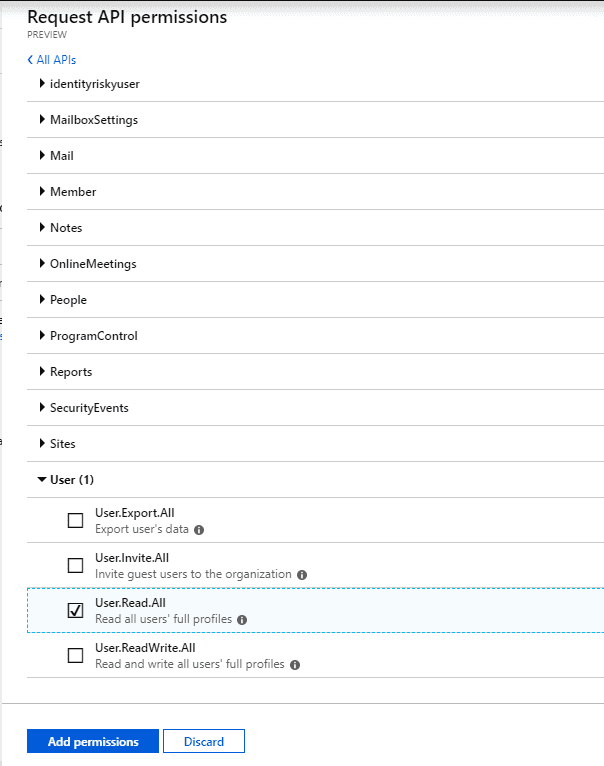
All the application needs is readonly access to users, so grab that.
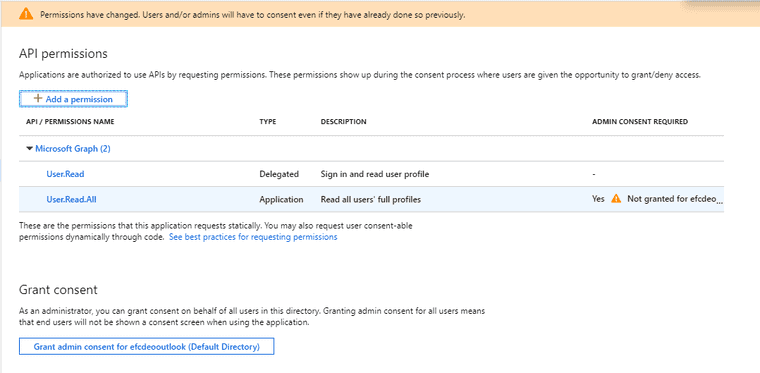
Azure will immediately comment that the application needs approval from an admin.
Go ahead and grant permissions using the button at the bottom of the screen.
Code
The code is using the credentials from the application registered above to request a Bearer Token and call the Azure GraphServiceClient.
using Microsoft.Graph;
using Microsoft.IdentityModel.Clients.ActiveDirectory;
using System;
using System.Net.Http.Headers;
namespace testGraphClient
{
class Program
{
static void Main(string[] args)
{
string clientID = ""; // Put the Application ID from above here.
string clientSecret = ""; // Put the Client Secret from above here.
string graphApiResource = "https://graph.microsoft.com";
Uri microsoftLogin = new Uri("https://login.microsoftonline.com/");
string tenantID = ""; // Put the Azure AD Tenant ID from above here.
// The authority to ask for a token: your azure active directory.
string authority = new Uri(microsoftLogin, tenantID).AbsoluteUri;
AuthenticationContext authenticationContext = new AuthenticationContext(authority);
ClientCredential clientCredential = new ClientCredential(clientID, clientSecret);
// Picks up the bearer token.
AuthenticationResult authenticationResult = authenticationContext.AcquireTokenAsync(graphApiResource, clientCredential).Result;
GraphServiceClient graphClient = new GraphServiceClient(new DelegateAuthenticationProvider(
async (requestMessage) =>
{
// This is adding a bearer token to the httpclient used in the requests.
requestMessage.Headers.Authorization = new AuthenticationHeaderValue("bearer", authenticationResult.AccessToken);
}));
IGraphServiceUsersCollectionPage users = graphClient.Users.Request().GetAsync().Result;
// I don't have many users, else I'd have to request the next page of results.
foreach (var user in users.CurrentPage)
{
Console.WriteLine("DisplayName: {0}", user.DisplayName);
}
}
}
}The results printed out to console will be the DisplayNames for each of your users. A sample given below of my results.
DisplayName: Daniel Test
DisplayName: Daniel OSummary
Actually calling the graph service is easy. Most of the difficulties come from not knowing where to register for and assign permissions. The quickstart references are here.